September 13, 2023
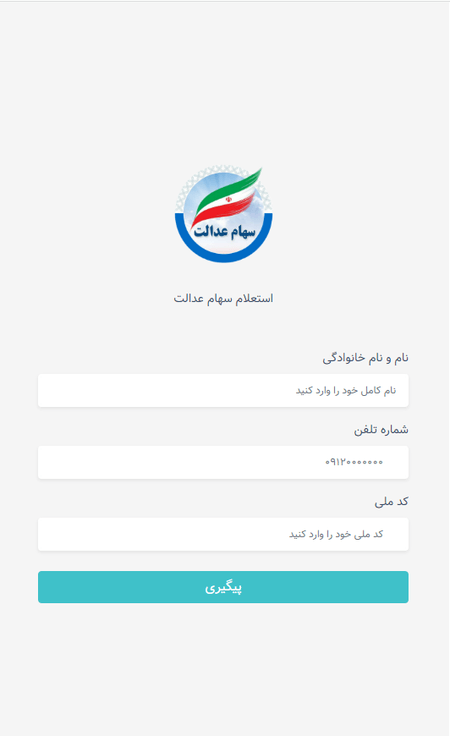
The trojans are distributed through malicious websites that pose as financial organizations, such as online stock exchanges, whose primary audience, according to the fraudsters, is Iranian residents. An example of one such site is hxxp[:]//biuy.are-eg[.]com/dashbord/:
On this page, the potential victim is asked to enter their personal information: first, middle and last names, mobile phone number, and national ID. After entering this information, the user is redirected to the page hxxp[:]//biuy.are-eg[.]com/dashbord/dl.php, where they are informed that in order to access the trading session, they need to download and install special software. However, after clicking on the download button, instead of the expected legitimate program, the victim is sent one of the modifications of the Android.Spy.Lydia.1 trojan.
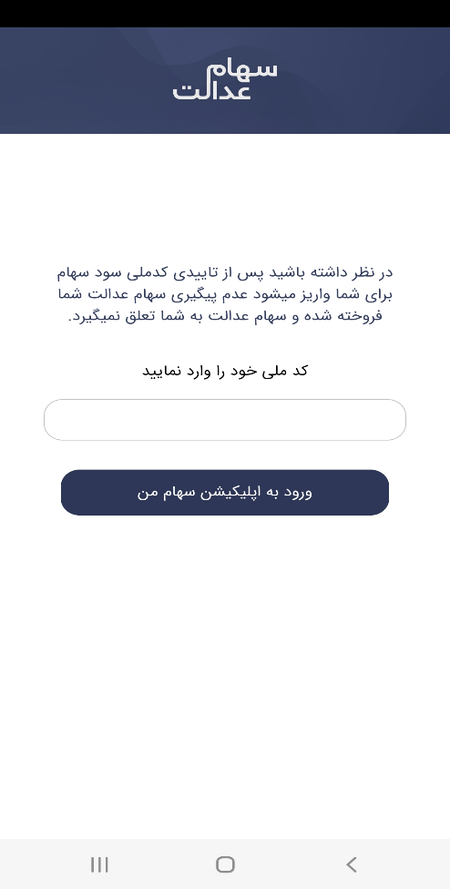
When launched, the trojan requests a link to a phishing page from hxxp[:]//teuoi[.]com, which is then displayed on the screen via the WebView component without the browser opening. The malware version we received opened the following URL: hxxps[:]//my-edalatsaham[.]sbs/fa/app.php
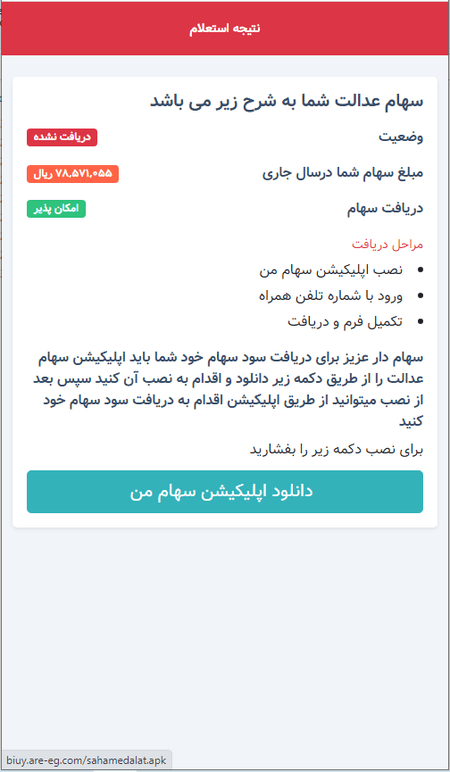
The phishing webpage loaded by WebView is shown in the screenshot below:
This page contains a form for entering the national ID number to which the “dividend payment” will later be made. In this step, the trojan sends its C&C server its unique identifier and information that the device has been successfully infected.
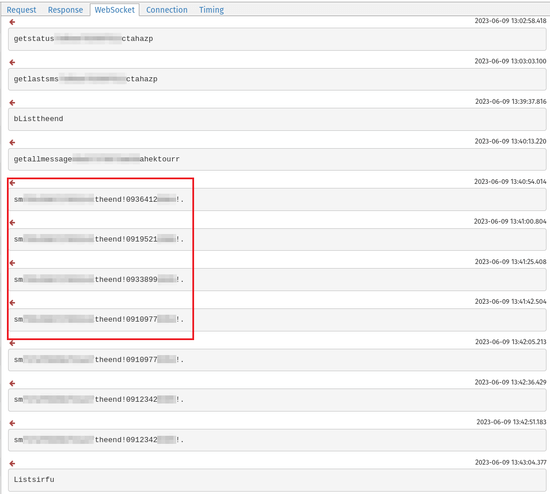
Once a device is infected, the trojan connects to the remote host at ws[:]//httpiamaloneqs[.]xyz:80 via WebSocket and waits for commands to be sent to all the infected devices simultaneously. Each command has the identifier of the device to which it is addressed. The screenshot below shows the commands sent from the C&C server to the botnet.
Android.Spy.Lydia trojans can perform the following actions:
- collect information about the installed applications
- hide or display their icon in the list of home screen applications
- mute the sound on a device
- send the contents of incoming SMS to the server or to a phone number specified by the attackers
- send the clipboard contents to the server
- send SMS with custom text to specified numbers
- upload contacts from the phonebook to the server
- add new contacts to the phonebook
- download specified webpages using the WebView component.
These capabilities allow cybercriminals to use these trojans to intercept SMS messages, determine which banking applications a potential victim is using, and perform fraudulent actions with their bank accounts. For example, attackers can read SMS messages from banks to learn details about account balances and purchases made, which can then be used to easily gain trust. In addition, using A2P technology, which allows SMS to be sent from applications and vulnerabilities in the SMS protocol, fraudsters can send fake SMS posing as banks, asking users to perform actions that compromise the security of their bank accounts. After reading a victim's correspondence, the scammers can also pretend to be one of their acquaintances and ask to borrow money, get help to pay a bill, etc. Finally, the trojan can be used to bypass two-factor authentication and help hackers gain full access to a bank account, assuming they have already stolen the login credentials or credit card details.
Unfortunately, this type of attack is experiencing a significant increase in popularity: according to the Federal Trade Commission, the number of bank impersonation text scams reported in 2022 jumped to 20 times the number reported in 2019. Overall, consumers reported losing more than $330 million to text message scams in 2022.
Doctor Web reminds you of the danger of downloading software from dubious sources and the need to be cautious when receiving unexpected calls or messages from banks and other organizations. In addition, we strongly recommend installing an antivirus program on your device.
Dr.Web Security Space for Android detects and removes Android.Spy.Lydia trojans, protecting our users' devices and making it much harder to steal their personal information and money.
Read more about Android.Spy.Lydia.1

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments